Phishing
What is phishing?
“Phishing” is a fraudulent attempt to obtain sensitive information such as usernames, passwords, and financial information by impersonating a trustworthy entity. Phishing is the single most common method of cyberattack. Phishing can come in the form of a phone call, an email, or a website. Most often, phishing attacks will ask you to click on a link, fill out a form, download a malicious file, or simply respond with some requested information.
Identifying phishing messages
There are a number of common signs of phishing:
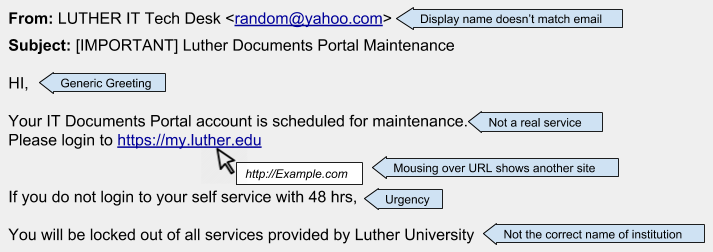
Sender’s display name doesn’t match email address
Hackers will often change the sender’s display name in an effort to make an email seem more legitimate. For example, a hacked account might masquerade as the Security office by simply changing the display name to “Campus Security”.
Generic greeting
Most phishing campaigns rely on volume rather than personalization. Phishing emails often aren’t addressed to you with appropriate familiarity. They might instead be addressed to “Sir or Madam”, “Mr…” or “Ms…”, or simply omit a name at all (e.g. “Dear,”).
Incorrect grammar, syntax, spelling
Phishing attacks sometimes use incorrect language. This is often deliberate: those who aren’t suspicious of blatant language problems are re-targeted in future attacks.
Sense of urgency
Attackers try to compel you to action before you have had time to become suspicious and use your better judgement. Content will often try to evoke fear, panic, and greed. Topics might be about resetting passwords, submitting paperwork, quickly fleeting windows of opportunity, or a “final notice”.
Unexpected
Generic phishing is always unexpected; spear phishing will try to blend in with normal life activities. If you aren’t expecting the communication, you should be suspicious.
Links and attachments
Most phishing attacks will try to get you to click on a link or download an attachment. It is never safe to do so: A malicious link or download could immediately allow malware to execute. Another possibility is that the link takes you to a page that outright asks you for credentials; no malware needed. These types of destination pages often try to emulate legitimate pages, like a Norse Key login page. Instead, inspect a link by copying or hovering over it. Specifically, notice whether the domain portion of the link is trustworthy. The domain is the portion of the URL that includes the suffix (.edu, .com, etc.) and everything up to the preceding period (e.g. https://subdomain. luther.edu /randompage.html)
What if I respond to a phishing message?
If you are the victim of a phishing message (i.e. clicked link, downloaded files, or responded), please reset your Norse Key immediately at norsekey.luther.edu and call the Technology Help Desk at 563-387-1000 for help re-securing your account.
Reporting a phishing message
Even if you didn’t interact with the phishing message beyond opening the message, you should report in two ways:
- Within the web version of Norse Mail, use the drop down menu next to “reply” and choose “Report phishing”.
- Report to the Technology Help Desk by either forwarding the email to helpdesk@luther.edu, calling 563-387-1000, or submitting a ticket at help.luther.edu.
Example phishing emails
Example: Impersonating Technology Help Desk
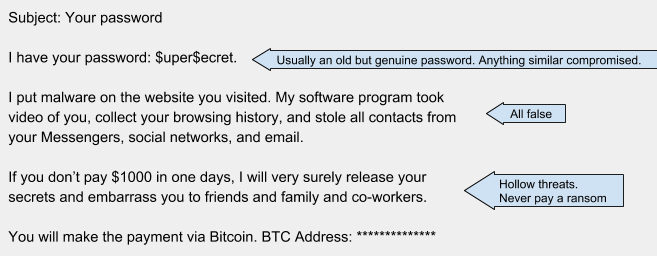
Example: Extortion
Protect yourself & Luther from targeted phishing attacks
Targeted phishing attacks are those designed to look familiar and/or legitimate. The following video created at the University of Michigan explains how these attacks are geared to users globally and on college campuses.
Technology Help Desk
Preus Library
Main Level
700 College Dr
Decorah, IA 52101
Summer Hours
May 23 – September 2
M-Th: 8:00 am – 5:00 pm
F: 8:00 am – 2:30 pm
Sa-Su: Closed
Closed Holidays: May 26, June 19, and July 4
helpdesk@luther.eduPhone: 563-387-1000